babyrsa
此题为有限域上不可约多项式的RSA,详情就看一下链接:
https://wenku.baidu.com/view/038968b632d4b14e852458fb770bf78a65293a37.html
解题分为四个步骤:
- factor n,得到p、q
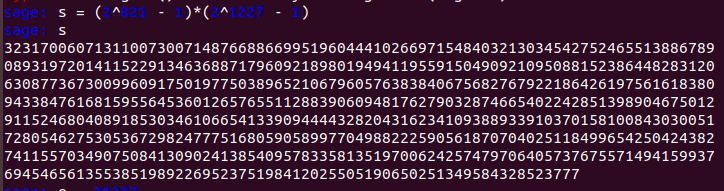
- 求s = (2 ^ 821 - 1) * (2 ^ 1227 - 1)
- 计算d,d = modinv(e,s)
- getflag,flag = pow(cipher, d, n)
第一步:
1 | sage: P=PolynomialRing(GF(2),'x') |
可以得到
1 | p = x^821 + x^820 + x^819 + x^818 + x^817 + x^814 + x^813 + x^812 + x^810 + x^808 + x^807 + x^804 + x^801 + x^796 + x^795 + x^794 + x^790 + x^787 + x^786 + x^784 + x^781 + x^780 + x^779 + x^778 + x^777 + x^776 + x^775 + x^774 + x^773 + x^771 + x^770 + x^768 + x^766 + x^762 + x^761 + x^760 + x^758 + x^757 + x^752 + x^749 + x^748 + x^747 + x^740 + x^737 + x^736 + x^732 + x^727 + x^723 + x^722 + x^719 + x^718 + x^717 + x^716 + x^715 + x^714 + x^711 + x^710 + x^708 + x^704 + x^703 + x^702 + x^701 + x^700 + x^699 + x^698 + x^696 + x^692 + x^690 + x^689 + x^687 + x^685 + x^683 + x^681 + x^676 + x^674 + x^672 + x^671 + x^670 + x^668 + x^667 + x^665 + x^664 + x^663 + x^661 + x^660 + x^659 + x^657 + x^656 + x^655 + x^651 + x^649 + x^646 + x^644 + x^637 + x^636 + x^634 + x^633 + x^632 + x^631 + x^628 + x^626 + x^625 + x^622 + x^621 + x^620 + x^614 + x^611 + x^609 + x^608 + x^605 + x^604 + x^599 + x^597 + x^592 + x^591 + x^589 + x^580 + x^578 + x^574 + x^572 + x^569 + x^566 + x^565 + x^563 + x^562 + x^560 + x^552 + x^550 + x^545 + x^544 + x^543 + x^542 + x^540 + x^538 + x^537 + x^534 + x^533 + x^528 + x^527 + x^526 + x^523 + x^522 + x^519 + x^518 + x^515 + x^514 + x^512 + x^505 + x^503 + x^502 + x^500 + x^498 + x^496 + x^493 + x^492 + x^491 + x^490 + x^489 + x^487 + x^482 + x^480 + x^479 + x^478 + x^476 + x^474 + x^472 + x^471 + x^470 + x^469 + x^468 + x^466 + x^462 + x^459 + x^458 + x^457 + x^456 + x^454 + x^453 + x^451 + x^449 + x^447 + x^445 + x^443 + x^442 + x^441 + x^440 + x^437 + x^434 + x^428 + x^425 + x^424 + x^423 + x^420 + x^415 + x^412 + x^411 + x^410 + x^408 + x^405 + x^404 + x^403 + x^401 + x^400 + x^394 + x^391 + x^390 + x^389 + x^388 + x^384 + x^383 + x^382 + x^379 + x^378 + x^376 + x^375 + x^372 + x^371 + x^370 + x^368 + x^366 + x^365 + x^364 + x^361 + x^358 + x^357 + x^356 + x^354 + x^351 + x^347 + x^345 + x^344 + x^340 + x^339 + x^335 + x^334 + x^333 + x^332 + x^331 + x^328 + x^326 + x^322 + x^318 + x^315 + x^312 + x^306 + x^303 + x^302 + x^301 + x^300 + x^299 + x^298 + x^297 + x^295 + x^293 + x^291 + x^289 + x^288 + x^287 + x^286 + x^285 + x^282 + x^280 + x^279 + x^277 + x^274 + x^273 + x^270 + x^269 + x^268 + x^263 + x^262 + x^261 + x^259 + x^258 + x^257 + x^256 + x^252 + x^250 + x^249 + x^245 + x^244 + x^243 + x^242 + x^236 + x^234 + x^233 + x^232 + x^228 + x^225 + x^223 + x^222 + x^221 + x^219 + x^218 + x^215 + x^214 + x^213 + x^211 + x^210 + x^209 + x^207 + x^205 + x^203 + x^202 + x^200 + x^198 + x^197 + x^193 + x^191 + x^190 + x^185 + x^184 + x^182 + x^180 + x^179 + x^177 + x^172 + x^168 + x^167 + x^165 + x^163 + x^161 + x^159 + x^157 + x^156 + x^155 + x^154 + x^153 + x^151 + x^150 + x^149 + x^148 + x^146 + x^145 + x^143 + x^139 + x^137 + x^136 + x^135 + x^133 + x^132 + x^130 + x^127 + x^126 + x^125 + x^124 + x^122 + x^121 + x^120 + x^119 + x^117 + x^116 + x^113 + x^111 + x^110 + x^109 + x^108 + x^107 + x^106 + x^105 + x^100 + x^97 + x^95 + x^89 + x^88 + x^87 + x^86 + x^85 + x^84 + x^82 + x^81 + x^80 + x^77 + x^76 + x^75 + x^74 + x^69 + x^67 + x^65 + x^61 + x^59 + x^57 + x^53 + x^52 + x^50 + x^49 + x^48 + x^45 + x^41 + x^40 + x^36 + x^34 + x^33 + x^27 + x^26 + x^24 + x^23 + x^22 + x^21 + x^20 + x^19 + x^18 + x^15 + x^14 + x^12 + x^9 + x^6 + x^4 + x^3 + x + 1 |
第二步
最终sage脚本:
1 | #!/usr/bin/env sage |
zer0lfsr
writeup:https://github.com/p4-team/ctf/tree/master/2019-03-23-0ctf-quals/crypto_lfsr
题目给了两个文件,一个是加密脚本,一个是加密结果
通过加密脚本我们可以看到flag是由三部分组成,我们的目标就是找到这三个init。刚开始看这道题目的时候,想到虽然可以知道每一次combine的结果是什么,但是要用此来推出x1、x2、x3也太多种可能了,然后就去吃饭了,后来看到z3约束求解器的存在
安装z3
1 | sudo pip install z3-solver |
writeup脚本如下:
1 | # -*- coding:utf8 -*- |
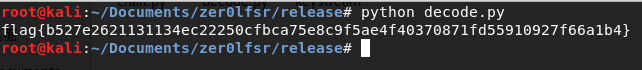
运行即可getflag
babysponge
writeup:https://github.com/p4-team/ctf/tree/master/2019-03-23-0ctf-quals/crypto_keccak
海绵函数:https://en.wikipedia.org/wiki/Sponge_function
有点懵,改天再来复现Orz…
zer0mi
writeup:https://github.com/miszcz2137/ctf-writeups/blob/master/0ctf2019/zer0mi/write-up.md
https://hxp.io/blog/52/0CTF-Quals-2019-zer0mi-writeup/
我太菜了,看不懂,改天再来复现