经过两天的国赛,学到了不少东西,本菜鸡是web手在比赛中搞成了密码选手Orz,记录一下密码
puzzles
这一题简单题,只要会解积分就很快了
flag格式:

question0:

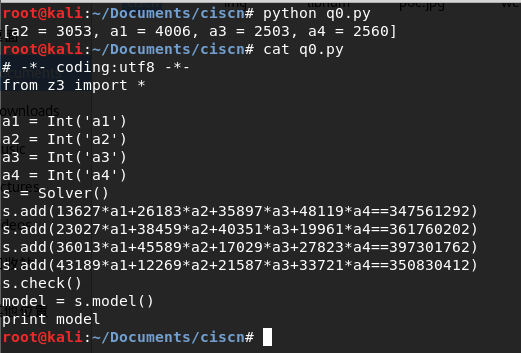
a1a2a3a4通过z3约束求解器解出
question1:
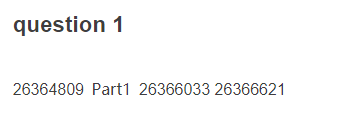
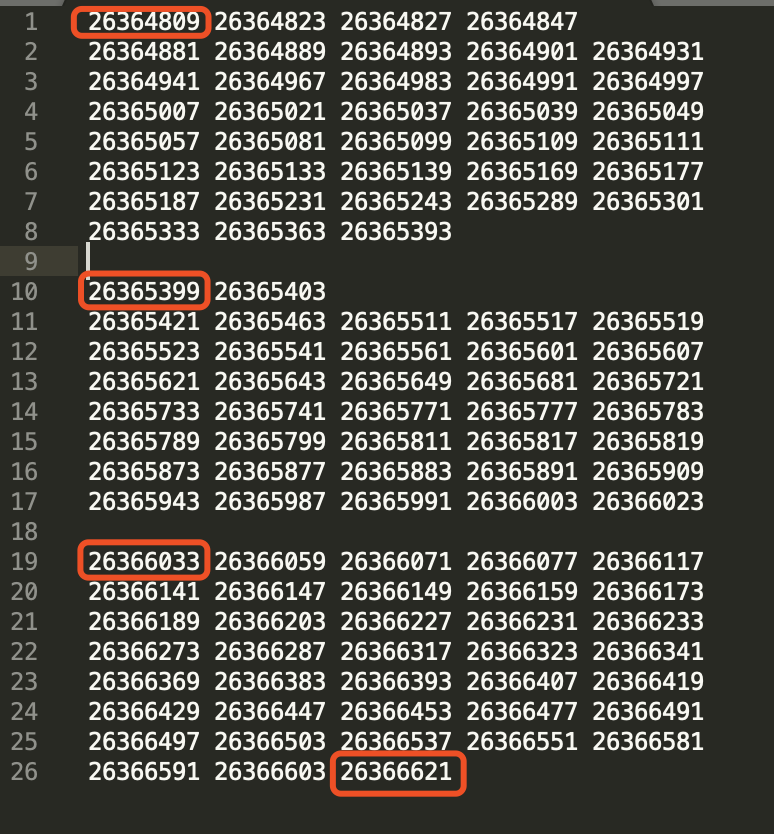
搜索条件给出的3个数字,都在一张质数表,找规律,每两个数间隔37个数,锁定26365399,Part1 = 26365399
question2:
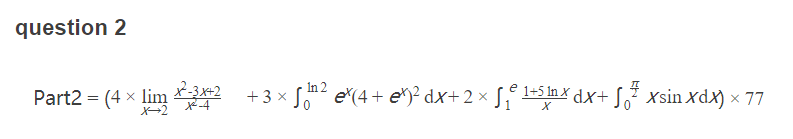
求积分求解得Part2 = 7700,不多说
question3:

电动势=2πrBdr/dt=2π×2×4×5=80πV,根据题目给出的已知条件求解得到Part3 = 18640
question4:
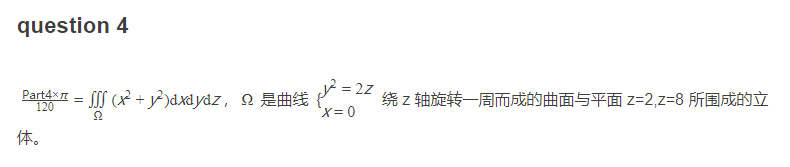
百度大法好,搜索得到答案336π,再根据题目已知条件求解得到Part4 = 40320
https://zhidao.baidu.com/question/330362706543929325.html
part_des
题目给了两个信息,一个是第n轮加密后的密文,第二个是加密过程中产生的16轮加密的子密钥,在DES加密算法中,子密钥都是通过密钥来生成的,那如果我们能得到密钥的话,我们使用密钥对任意8位明文进行加密,在第n轮修改他的子密文,然后将加密后的最终密文解密即可得到flag。
那我们可不可以通过子密钥来反推出密钥呢?答案是可以的:
反推密钥脚本:
1 | Kn = [ |
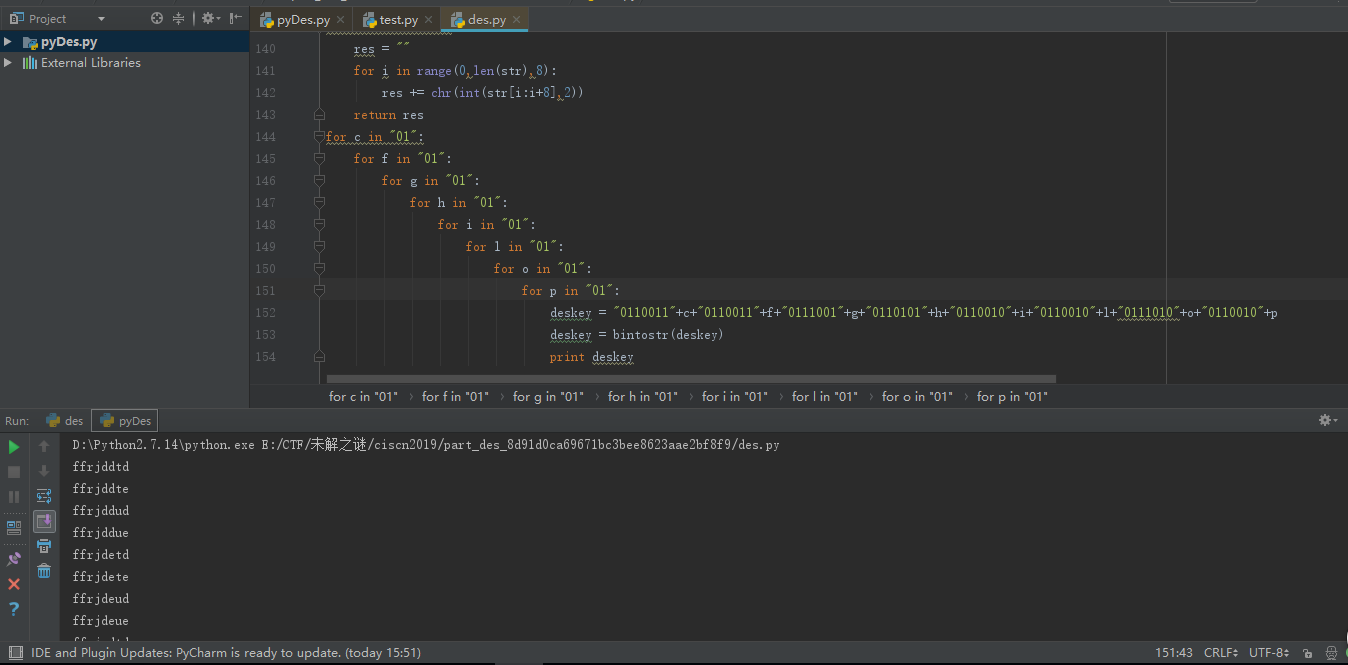
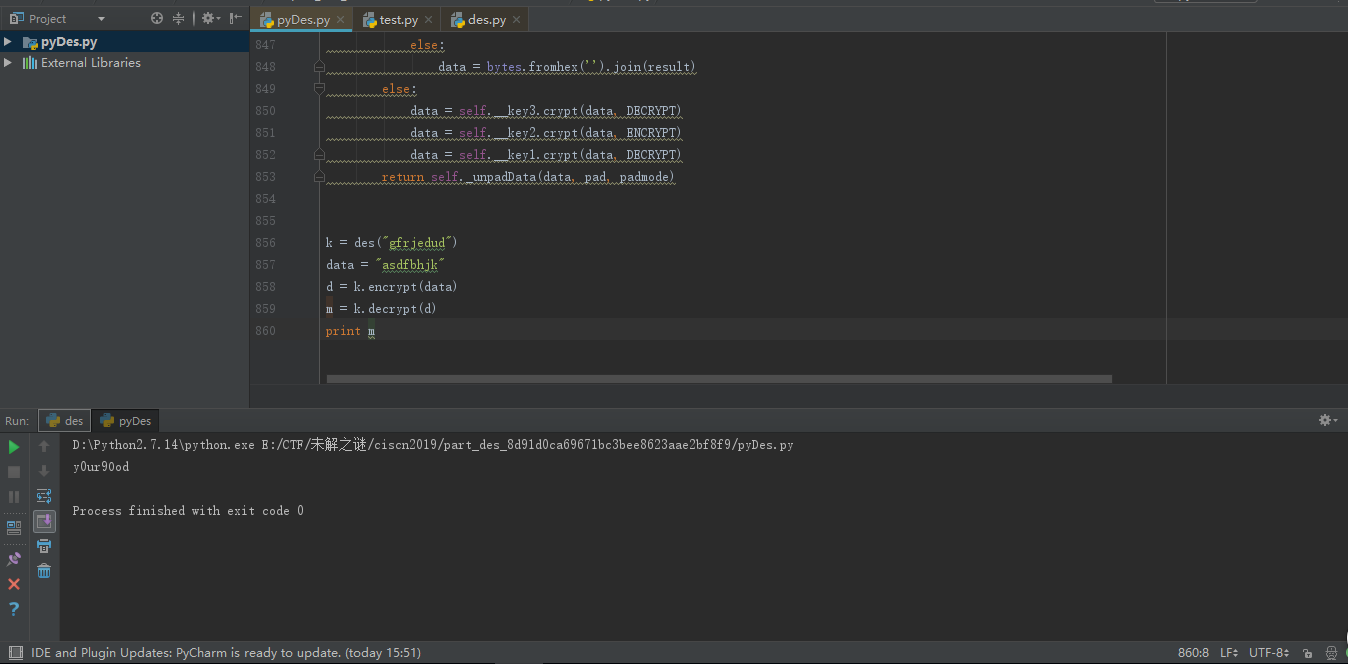
运行脚本可以得到无数个key,接下来就是修改pyDES脚本getflag,脚本太长了,就贴个修改部分
1 | def __des_crypt(self, block, crypt_type): |
warmup
打开看到是AES CTR加密模式,该模式存在一个缺点:主动攻击(改明文,后续内容不影响,只要误差不传递该缺点就存在)
操作流程:
- 连接服务器,第一次什么都不输入,获得第一条密文c1,知道flag加密后的密文有48个字节
- 第二次输入1111111111111111(16个1),获得第二条密文c2
- 第三次输入11111111111111111111111111111111(32个1),获得第三条密文c3
- 第四次输入111111111111111111111111111111111111111111111111(48个1),获得第四条密文c4
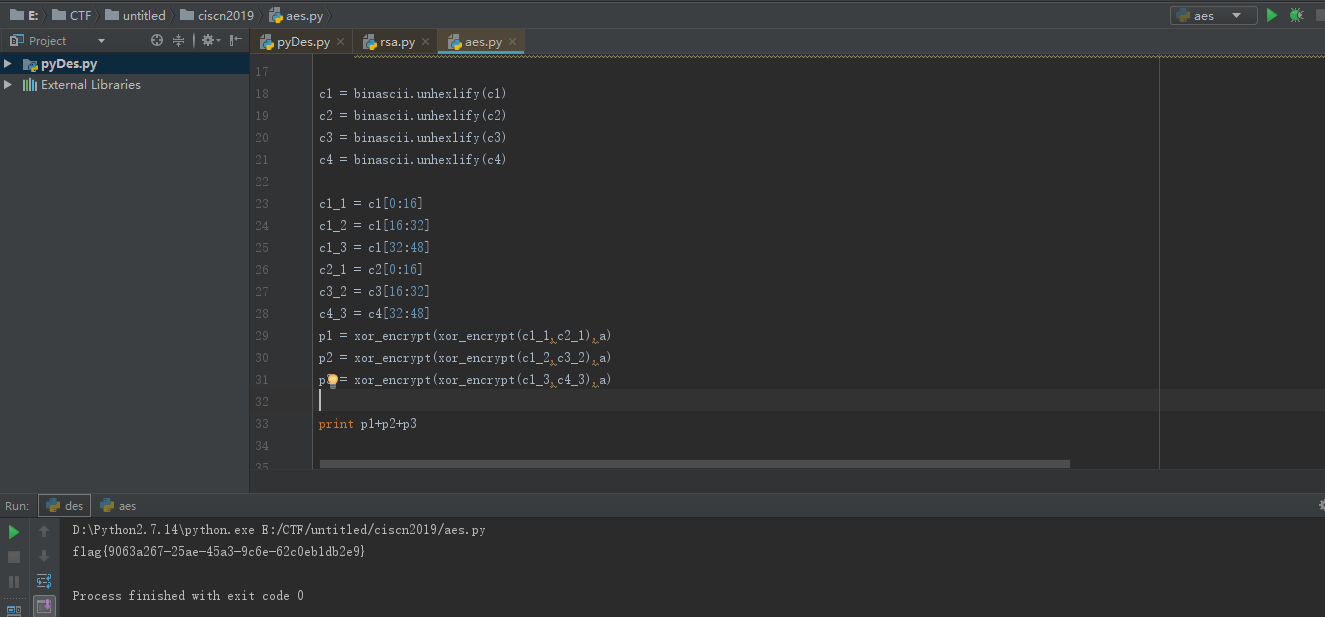
- 将c1[0:16]与c2[0:16]异或再与1111111111111111异或得到flag第一部分
- 将c1[16:32]与c3[16:32]异或再与1111111111111111异或得到flag第二部分
- 将c1[32:48]与c3[32:48]异或再与1111111111111111异或得到flag第三部分
脚本:
1 | import binascii |
Asymmetric
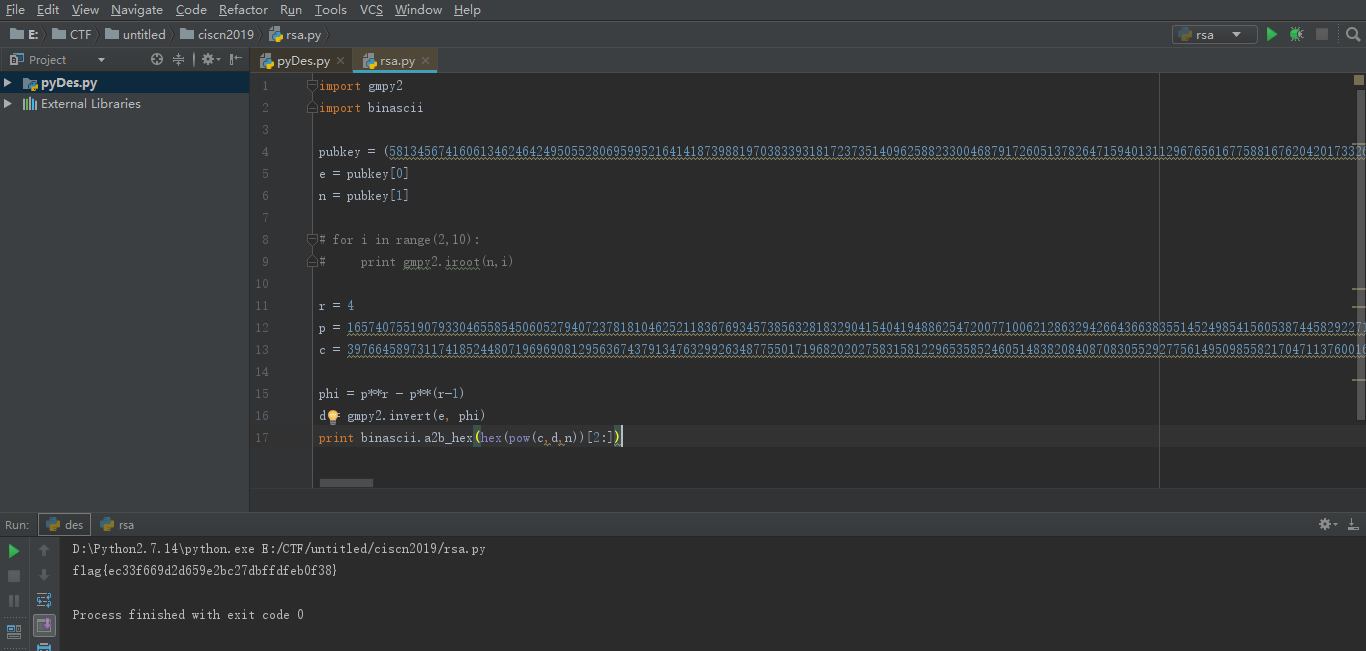
这题是一道rsa,n = p**r,r在2-10,并且n已知,因此可以使用gmpy2.iroot函数爆破得到
1 | r = 4 |
因为p为质数,因此欧拉函数φ(p^r)=p^r-p^(r-1),知道欧拉函数和e,那么就可以求出d,从而求出flag
脚本如下:
1 | import gmpy2 |