Web没什么好写的…主要记录一下rsa方面的操作
copperstudy
1 | import hashlib |
第一关,已知明文m高位
1 | n = 0x21b23a088ed1aadf9cfd65ccfd9002920f451be3bd25809eb926d5ee63ec3640285867836aa265843832d544a653c9107fcbee6aea10dbee68ab197c83f777f8cab7490d848bf6f93c04f255f7c4c2bff40a299af7b6651e6849cf51b7483b413c6c4a318f65cac0bdc2ddcbf35a46f84f64b6c8351eedb83004c0710d74ba67 |
第二关,已知高位p
1 | from sage.all import * |
第三关,e较小,已知d的低位,Partial Key Exposure Attack(部分私钥暴露攻击)
1 | def partial_p(p0, kbits, n): |
第四关,使用不同的模数n,相同的公钥指数e加密相同的信息,广播攻击。一般会是e=k,然后给k组数据,使用中国剩余定理
1 | import gmpy2 |
第五关,n相同,明文相差1大部分相同,可进行 Coppersmith’s Short Pad attack和 Franklin-Reiter related messages attack
1 | def short_pad_attack(c1, c2, e, n): |
第六关,知道n、e、c,并且e很大,Boneh and Durfee attack
我们知道,如果要使用Wiener’s Attack,则d要满足以下条件
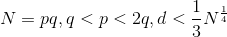
那如果e很大,但是d比上述要大,那就可以尝试Boneh and Durfee attack,条件为
1 | d < N^0.292 |
使用以下这个脚本就可以求出d
https://github.com/Gao-Chuan/RSA-and-LLL-attacks/blob/master/boneh_durfee.sage
强网先锋_辅助
知道n1、n2、c1、c2、e,q不变,因此通过求n1、n2的公约数得到q,从而得到p1,进而得到flag
1 | import gmpy2 |